Introduction
SMTP smuggling is a novel vulnerability that allows e-mail spoofing by exploiting interpretation differences of the SMTP protocol in vulnerable server constellations. More specifically, different understandings of so called "end-of-data" sequences between outbound (sending) and inbound (receiving) SMTP servers may allow an attacker to smuggle - hence SMTP smuggling - spoofed e-mails (see Figure 1). Threat actors can abuse this to send malicious e-mails from arbitrary e-mail addresses, allowing targeted phishing attacks.
Affected software identified on the outbound side includes Exchange Online and GMX, which are hosting millions of domains. On the inbound side, over a million SMTP instances including Postfix, Sendmail, Cisco and others are affected. This allowed spoofing e-mails from millions of domains (e.g., microsoft.com, github.com, gmx.net) to millions of SMTP servers.
As a result of miscommunications in the vulnerability disclosure, millions of inbound SMTP servers are left vulnerable to SMTP smuggling. Further cases of SMTP smuggling vulnerabilities in outbound servers would again allow spoofing e-mails from affected domains.
Also due to a severe case of SMTP smuggling in Cisco Secure Email and missing vendor support, it is highly advised to change the vulnerable default configuration (see affected software).
In-depth information on SMTP smuggling can be found in the original blog post as well as in the referenced resources. The official CERT/CC vulnerability note (VU#302671) can be found here.
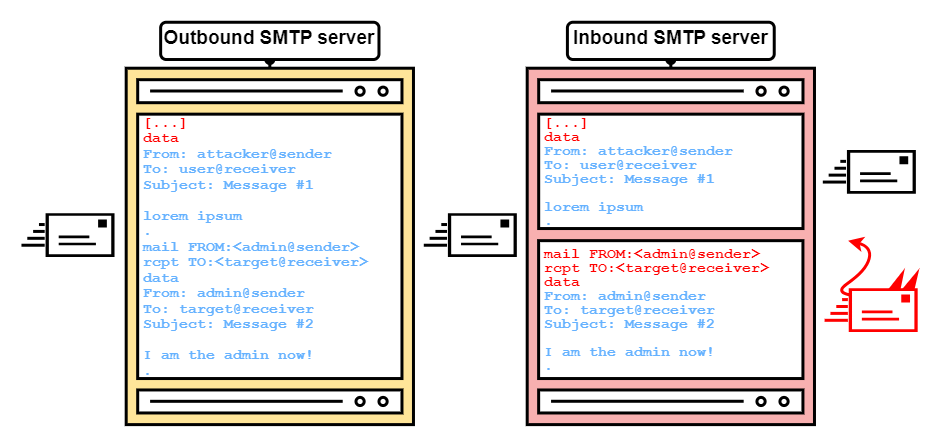
Figure 1: SMTP smuggling overview
Tools
Here are some tools for identifying SMTP smuggling issues that are available on GitHub!
"Official" SMTP smuggling tools:
View SMTP Smuggling Tools on GitHubThank you Hanno Böck for smtpsmug!
View smtpsmug on GitHubI'm vulnerable! What now?
The Affected Software section may include the information you are looking for. Furthermore, there may already be fixes and workarounds for your specific SMTP software online.
If you don't find any solutions online, please create an issue on GitHub.
Affected Software
Official vendor statements can be found in CERT/CC's vulnerability note. However, keep in mind that there are "different views" on the vulnerability (e.g., Cisco).
| Software | Description | Fix/Workaround | Smuggling direction | CVE |
|---|---|---|---|---|
| Cisco Secure Email (Cloud) Gateway | On-premise and cloud versions of Cisco Secure Email Gateway using the default configuration are vulnerable to severe inbound SMTP smuggling, since end-of-data sequences like "<CR>.</CR>" are accepted. This allows spoofing e-mails from millions of domains. More information can be found in the original blog post. | UPDATE: The updated CR and LF handling setting now adds an X-header to a message, if an invalid end-of-data sequence is received. Messages with such a header can furthermore be handled with content filter policies, as described here. The "Allow" option is also no more deprecated, which now allows to avoid the "Clean" option (which enables SMTP smuggling) and the "Reject" option (which drops all messages that do not fully adhere to RFCs in terms of CRs and LFs). |
Inbound | - |
| Postfix | Postfix was identified to accept non RFC-compliant end-of-data sequences like "<LF>.<CR><LF>". This is not as severe of an issue like with Cisco Secure Email, however this still allows SMTP smuggling, if outbound servers (as identified with Exchange Online and GMX) do not filter such "<LF>.<CR><LF>" sequences. More information can be found in the original blog post. | Detailed information can be found on the Postfix website. Thanks to Wietse and Viktor for providing quick solutions! |
Inbound | CVE-2023-51764 |
| Sendmail | Sendmail and Postfix handle end-of-data sequences the same way. As with Postfix, pipelined SMTP commands by default get executed after a "fake" end-of-data sequence is processed. | For now, Sendmail snapshot 8.18.0.2 can be used. More information can be found here. | Inbound | CVE-2023-51765 |
| Exim | Some configurations of Exim are vulnerable to SMTP smuggling similar to Postfix and Sendmail. | Upgrading to Exim version 4.97.1 or later should fix this issue. More information can be found on the Exim website. | Inbound | CVE-2023-51766 |
| aiosmtpd | aiosmtpd is vulnerable to SMTP smuggling similar to Postfix and Sendmail. | Upgrading to aiosmtpd version 1.4.5 or later should fix this issue. More information can be found on GitHub. | Inbound | CVE-2024-27305 |
| SurgeMail | SurgeMail is vulnerable to SMTP smuggling similar to Postfix and Sendmail. | More information on fixing SurgeMail can be found on the SurgeMail website. | Inbound | - |
| Exchange Online | Outbound Exchange Online servers allowed to send "<LF>.<CR><LF>" sequences to inbound/receiving servers due to insufficient filtering of message data. This behavior is a violation of RFC 5322 and, as of now, was only identified for Exchange Online and GMX (see below). This vulnerability allowed smuggling spoofed e-mails from millions of domains hosted at Exchange Online (e.g., microsoft.com, github.com, tesla.com, etc.) to millions of e-mail servers running Postfix, Sendmail, Exim and possibly more. | Microsoft has already fixed this issue. | Outbound | - |
| GMX | As Exchange Online, GMX also allowed to send "<LF>.<CR><LF>" sequences to millions of inbound/receiving servers due to insufficient filtering of message data. | GMX promptly fixed this issue. | Outbound | - |
| Possibly more! | Please help us to identify more vulnerable SMTP software by using the provided tools. If you're vulnerable and using software that is not already in this list, please create an issue on GitHub. |
Unaffected Software
Here is a list of software that was confirmed to be unaffected by SMTP smuggling.
However, keep in mind that constellations with multiple SMTP servers could again introduce SMTP smuggling issues.
| Software | Description |
|---|---|
| qmail | Vanilla qmail was confirmed to be unaffected by SMTP smuggling. |
References
| Resource | Link |
|---|---|
| Original blog post | https://sec-consult.com/blog/detail/smtp-smuggling-spoofing-e-mails-worldwide/ |
| CERT/CC Vulnerability Note VU#302671 | https://www.kb.cert.org/vuls/id/302671 |
| Postfix status | https://www.postfix.org/smtp-smuggling.html |
| Cisco status | https://bst.cisco.com/quickview/bug/CSCwh10142 |
| SMTP smuggling and Exchange (DE) | https://www.msxfaq.de/internet/smtp_smuggling_exchange.htm |
| Email spoofing | https://en.wikipedia.org/wiki/Email_spoofing |
| Talk at 37C3 | https://www.youtube.com/watch?v=V8KPV96g1To |
Videos
Contribute
Want to make changes to this website? Great, contributions are highly appreciated! Please create issues and pull requests on GitHub.
Coming soon...
New information, updates, tools and more coming soon!
Imprint
company name SEC Consult Unternehmensberatung GmbH
business purpose IT-Dienstleistungen / Unternehmensberatung
VAT number ATU56165223
tax number 330 214 628
registration number FN 227896t
commerical court Handelsgericht Wien
DVR 3004017
address Wagramer Straße 19 / Stock 16 | 1220 Wien
eMail office(at)sec-consult.com
phone +4318903043 0
web www.sec-consult.com
membership of chamber of commerce Wirtschaftskammer Wien Fachgruppe: Unternehmensberatung und Informationstechnologie
applicable law Gewerbeordnung
management Wolfgang Baumgartner
data protection officer dpo-austria(at)atos.net
Privacy Policy
This website is hosted via GitHub Pages! Please refer to GitHub's privacy statement and data collection methods.